The battery breakthrough of the future and seemed like it always will be, is getting closer to the present with Toyota’s development. Electric car tech is ever-improving, as more and more manufacturers move away from ICE vehicles and more towards a future involving just EVs and hybrids. One company that you know will have a solid EV future is Toyota, being one of the world’s biggest car companies with the greatest success in… Source link
Read More »Monthly Archives: January 2021
Eugene Mallove, Scientist, Murdered After Housing Dispute
After a beloved scientist was found dead in Norwich, Connecticut in 2004, his killers were able to evade justice for more than four years. How? On the evening of May 14, Norwich police received a call that a dead body had been found at a local house. Upon their arrival, they found the victim, a man in his 50s, lying in a pool of his own blood. It was clear he had been viciously beaten, and there were even shoe patterns on his clothing, indicating someone may have stomped on him. “It was a horrific scene,” Joe Dolan, a retired detective with the Norwich PD, told Oxygen’s “An Unexpected Killer,” airing Fridays at 8/7c on Oxygen. The victim’s shoes and wallet were missing, and there was blood on multiple parts of the property, suggesting the struggle had… Source link
Read More »Why Everyone Will Be Right About GME, But Still End Up Losing Everything
Everyone is talking about GameStop (NYSE:), but how can you not when we are witnessing something we will likely never see again in our lifetimes? If GME at $40 seemed ridiculous, then $100 is absolutely bonkers. And I can’t even begin to think of a word that adequately describes the $483 it reached. If someone told me a stock would explode 2,463% in four short weeks, surely they just cured cancer, cracked the code for cold fusion, or invented an anti-gravity machine. Obviously, whatever they did, it would change life as we know it. Yeah, no. GME is a pedestrian company that sells used video games on physical disks. And not only did this company not cure some great ailment, it probably won’t even survive long enough to see the 2024 Paris Olympics. That probably explains why the… Source link
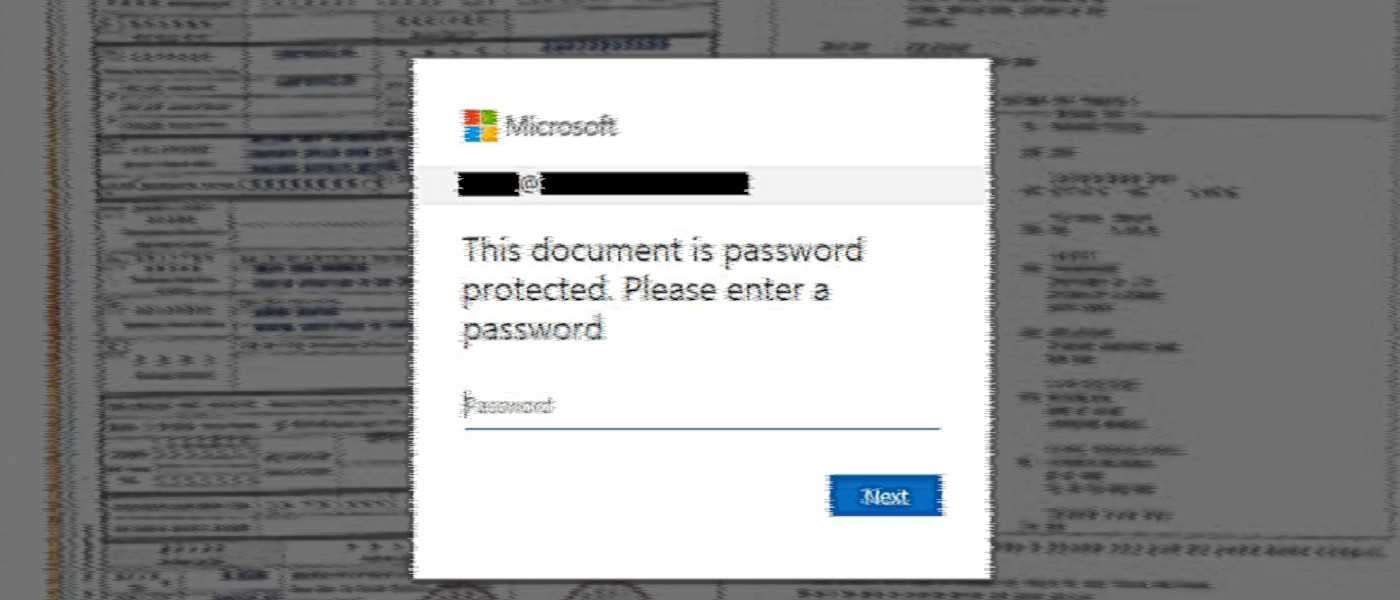
Read More »LogoKit Simplifies Office 365, SharePoint 'Login' Phishing Pages – Threatpost
A phishing kit has been found running on at least 700 domains – and mimicking services via false SharePoint, OneDrive and Office 365 login portals. A newly-uncovered phishing kit, dubbed LogoKit, eliminates headaches for cybercriminals by automatically pulling victims’ company logos onto the phishing login page. This gives attackers the tools needed to easily mimic company login pages, a task that can sometimes be complex. Cybercriminals have relied on LogoKit to launch phishing attacks on more than 700 unique domains over the past 30 days (including 300 in the past week). These targeted services range from generic login portals to false SharePoint, Adobe Document Cloud, OneDrive, Office 365, and cryptocurrency exchange login… Source link
Read More »Is the Dream of Cold Fusion Still a Possibility?
Back in March 1989, at a press conference in Salt Lake City, scientists Stanley Pons of the University of Utah and Martin Fleischmann of Great Britain’s University of Southampton made a startling announcement. The researchers had managed to fuse the atomic nuclei of a hydrogen isotope to create helium — the same sort of process that powers the sun — and they’d been able to do it at room temperature, without putting in more energy than the process produced, as this Wired retrospective from 2009 details. The research raised hopes of a new source of abundant energy that would replace fossil fuels and conventional nuclear power, as a CBS News story from that time reported. But other researchers who tried to duplicate the experiments were unable to reproduce… Source link
Read More »Is the Dream of Cold Fusion Still a Possibility?
In Europe, a multinational team of scientists recently embarked upon yet another cold fusion investigation, the HERMES project, which will employ more advanced scientific techniques and tools developed in recent years. “The purpose is to try to look for an experiment that would reproducibly produce some anomalous effects,” says Pekka Peljo, in an email. He’s the project’s coordinator, and an associate professor in the Department of Mechanical and Materials Engineering at the University of Turku in Finland. “We are revisiting some of the previous experiments. Also, we are going to study electrochemistry of palladium-hydrogen and palladium-deuterium systems in detail, utilizing well-controlled model systems such as palladium single crystals. So shortly,… Source link
Read More »Hacker blunder leaves stolen passwords exposed via Google search
Hackers hitting thousands of organizations worldwide in a massive phishing campaign forgot to protect their loot and let Google the stolen passwords for public searches. The phishing campaign has been running for more than half a year and uses dozens of domains that host the phishing pages. It received constant updates to make the fraudulent Microsoft Office 365 login requests look more realistic. Creds in plain sight Despite relying on simple techniques, the campaign has been successful in bypassing email protection filters and collected at least 1,000 login credentials for corporate Office 365 accounts. Researchers at cybersecurity companies Check Point and Otorio analyzing this campaign discovered that the hackers exposed the stolen credentials to the public internet. In a… Source link
Read More »Security researchers earn $50k after exposing critical flaw in Apple travel portal
Chained exploit leads to shell access Security researchers have earned a $50,000 bug bounty after uncovering a critical flaw in Apple’s travel portal. Rahul Maini and Harsh Jaiswal were able to achieve remote code execution (RCE) by stringing together a string of vulnerabilities in order to exploit targeted domains. The bug hunting exercise was inspired by earlier work by Sam Curry and his associates that uncovered no fewer than 55 vulnerabilities in Apple’s web infrastructure, earning a cumulative bug bounty of $288,000. Curry is continuing his work and this week went public with vulnerabilities in Apple’s domain that created a means to get billing data from any Apple user. Lucee in the sky with exploits In a detailed technical write-up, Maini… Source link
Read More »Cloud Attacks Are Bypassing MFA, Feds Warn – Threatpost
CISA has issued an alert warning that cloud services at U.S. organizations are being actively and successfully targeted. The Feds are warning that cybercriminals are bypassing multi-factor authentication (MFA) and successfully attacking cloud services at various U.S. organizations. According to an alert issued Wednesday by the Cybersecurity and Infrastructure Security Agency (CISA), there have been “several recent successful cyberattacks” focused on compromising the cloud. Most of the attacks are opportunistic, taking advantage of poor cloud cyber-hygiene and misconfigurations, according to the agency. “These types of attacks frequently occurred when victim organizations’ employees worked remotely and used a mixture of… Source link
Read More »Researcher Builds Parler Archive Amid Amazon Suspension – Threatpost
A researcher scraped and archived public Parler posts before the conservative social networking service was taken down by Amazon, Apple and Google. A security researcher said she has scraped and is archiving 99 percent of Parler’s public posts, as the social-media network goes offline following suspensions from Amazon, Apple and Google. Archived content includes public posts from the social-media site. These posts reportedly included Parler video URLs made up of raw video files with associated embedded metadata – and precise GPS coordinates of where the videos were taken, sparking privacy concerns about the service’s data collection. The researcher behind the archival… Source link
Read More »