Photo Courtesy of Xu Yu/Xinhua/Sipa USA/TNS Chinese Go player Ke Jie, third from right, and other guests attend the opening ceremony of the Future of Go Summit before a match between him and Google’s artificial intelligence program AlphaGo in China on May 23, 2017. Columnist Clint argues we must be careful when developing artificial intelligence. The year 2020 was, well, terrible … in many ways. The COVID-19 pandemic brought the entire world to a near standstill, and millions have either been infected or killed by the virus. The economies of many major countries are now in recession, with millions having lost their jobs in the United States alone. And, to top it all off, 2020 was the year we lost one of the greatest musical geniuses of all time — and my personal guitar hero —
Read More »A full-scale prototype for muon tomography — ScienceDaily
Each year, billions of tons of goods are transported globally using cargo containers. Currently, there are concerns that this immense volume of traffic could be exploited to transport illicit nuclear materials, with little chance of detection. One promising approach to combating this issue is to measure how goods interact with charged particles named muons — which form naturally as cosmic rays interact with Earth’s atmosphere. Studies worldwide have now explored how this technique, named ‘muon tomography,’ can be achieved through a variety of detection technologies and reconstruction algorithms. In this article of EPJ Plus, a team headed by Francesco Riggi at the University of Catania, Italy, build on these results to develop a full-scale muon tomograph… Source link
Read More »New Cryptojacking Malware Targeting Apache, Oracle, Redis Servers
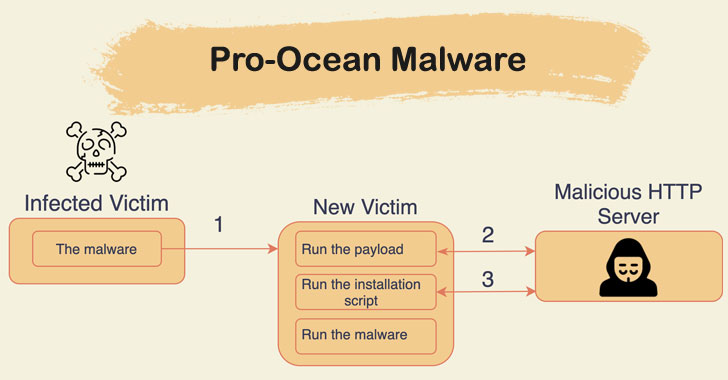
A financially-motivated threat actor notorious for its cryptojacking attacks has leveraged a revised version of their malware to target cloud infrastructures using vulnerabilities in web server technologies, according to new research. Deployed by the China-based cybercrime group Rocke, the Pro-Ocean cryptojacking malware now comes with improved rootkit and worm capabilities, as well as harbors new evasion tactics to sidestep cybersecurity companies’ detection methods, Palo Alto Networks’ Unit 42 researchers said in a Thursday write-up. “Pro-Ocean uses known vulnerabilities to target cloud applications,” the researchers detailed. “In our analysis, we found Pro-Ocean targeting Apache ActiveMQ (CVE-2016-3088), Oracle WebLogic (CVE-2017-10271) and Redis (unsecure instances).” “Once… Source link
Read More »Uncommon Science – Experimental Frontiers, with Josh Mitteldorf
The scientific method is built on two pillars: First, the assumption of a common objective reality that separate observers can agree on. Second, the understanding of complex phenomena by isolating simple subsystems for experimental study. In a quantum world, (first) it is provably impossible to separate observer from observed. There is no such thing as objective reality. And (second) it is possible to isolate a particle and do experiments, but most of the interesting quantum effects depend on collective properties of many identical particles that we can never probe by studying one-particle-at-a-time. Since these two pillars of the scientific method fell in the 1920s, scientists continue to think in terms of objective reality, and we continue to analyze pieces to understand the whole…. Source link
Read More »Toyota Set For Electric Revolution With New Solid State Battery
The battery breakthrough of the future and seemed like it always will be, is getting closer to the present with Toyota’s development. Electric car tech is ever-improving, as more and more manufacturers move away from ICE vehicles and more towards a future involving just EVs and hybrids. One company that you know will have a solid EV future is Toyota, being one of the world’s biggest car companies with the greatest success in… Source link
Read More »Eugene Mallove, Scientist, Murdered After Housing Dispute
After a beloved scientist was found dead in Norwich, Connecticut in 2004, his killers were able to evade justice for more than four years. How? On the evening of May 14, Norwich police received a call that a dead body had been found at a local house. Upon their arrival, they found the victim, a man in his 50s, lying in a pool of his own blood. It was clear he had been viciously beaten, and there were even shoe patterns on his clothing, indicating someone may have stomped on him. “It was a horrific scene,” Joe Dolan, a retired detective with the Norwich PD, told Oxygen’s “An Unexpected Killer,” airing Fridays at 8/7c on Oxygen. The victim’s shoes and wallet were missing, and there was blood on multiple parts of the property, suggesting the struggle had… Source link
Read More »Why Everyone Will Be Right About GME, But Still End Up Losing Everything
Everyone is talking about GameStop (NYSE:), but how can you not when we are witnessing something we will likely never see again in our lifetimes? If GME at $40 seemed ridiculous, then $100 is absolutely bonkers. And I can’t even begin to think of a word that adequately describes the $483 it reached. If someone told me a stock would explode 2,463% in four short weeks, surely they just cured cancer, cracked the code for cold fusion, or invented an anti-gravity machine. Obviously, whatever they did, it would change life as we know it. Yeah, no. GME is a pedestrian company that sells used video games on physical disks. And not only did this company not cure some great ailment, it probably won’t even survive long enough to see the 2024 Paris Olympics. That probably explains why the… Source link
Read More »LogoKit Simplifies Office 365, SharePoint 'Login' Phishing Pages – Threatpost
A phishing kit has been found running on at least 700 domains – and mimicking services via false SharePoint, OneDrive and Office 365 login portals. A newly-uncovered phishing kit, dubbed LogoKit, eliminates headaches for cybercriminals by automatically pulling victims’ company logos onto the phishing login page. This gives attackers the tools needed to easily mimic company login pages, a task that can sometimes be complex. Cybercriminals have relied on LogoKit to launch phishing attacks on more than 700 unique domains over the past 30 days (including 300 in the past week). These targeted services range from generic login portals to false SharePoint, Adobe Document Cloud, OneDrive, Office 365, and cryptocurrency exchange login… Source link
Read More »Is the Dream of Cold Fusion Still a Possibility?
Back in March 1989, at a press conference in Salt Lake City, scientists Stanley Pons of the University of Utah and Martin Fleischmann of Great Britain’s University of Southampton made a startling announcement. The researchers had managed to fuse the atomic nuclei of a hydrogen isotope to create helium — the same sort of process that powers the sun — and they’d been able to do it at room temperature, without putting in more energy than the process produced, as this Wired retrospective from 2009 details. The research raised hopes of a new source of abundant energy that would replace fossil fuels and conventional nuclear power, as a CBS News story from that time reported. But other researchers who tried to duplicate the experiments were unable to reproduce… Source link
Read More »Is the Dream of Cold Fusion Still a Possibility?
In Europe, a multinational team of scientists recently embarked upon yet another cold fusion investigation, the HERMES project, which will employ more advanced scientific techniques and tools developed in recent years. “The purpose is to try to look for an experiment that would reproducibly produce some anomalous effects,” says Pekka Peljo, in an email. He’s the project’s coordinator, and an associate professor in the Department of Mechanical and Materials Engineering at the University of Turku in Finland. “We are revisiting some of the previous experiments. Also, we are going to study electrochemistry of palladium-hydrogen and palladium-deuterium systems in detail, utilizing well-controlled model systems such as palladium single crystals. So shortly,… Source link
Read More »