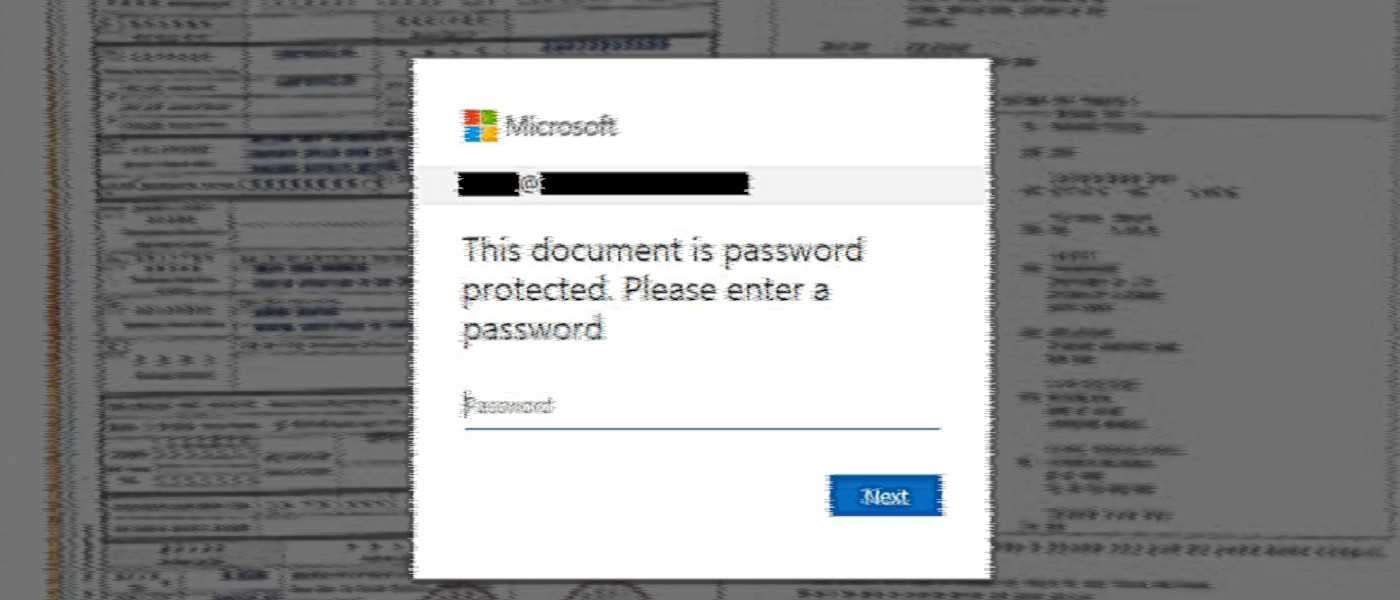
Hackers hitting thousands of organizations worldwide in a massive phishing campaign forgot to protect their loot and let Google the stolen passwords for public searches. The phishing campaign has been running for more than half a year and uses dozens of domains that host the phishing pages. It received constant updates to make the fraudulent Microsoft Office 365 login requests look more realistic. Creds in plain sight Despite relying on simple techniques, the campaign has been successful in bypassing email protection filters and collected at least 1,000 login credentials for corporate Office 365 accounts. Researchers at cybersecurity companies Check Point and Otorio analyzing this campaign discovered that the hackers exposed the stolen credentials to the public internet. In a… Source link
Read More »Security researchers earn $50k after exposing critical flaw in Apple travel portal
Chained exploit leads to shell access Security researchers have earned a $50,000 bug bounty after uncovering a critical flaw in Apple’s travel portal. Rahul Maini and Harsh Jaiswal were able to achieve remote code execution (RCE) by stringing together a string of vulnerabilities in order to exploit targeted domains. The bug hunting exercise was inspired by earlier work by Sam Curry and his associates that uncovered no fewer than 55 vulnerabilities in Apple’s web infrastructure, earning a cumulative bug bounty of $288,000. Curry is continuing his work and this week went public with vulnerabilities in Apple’s domain that created a means to get billing data from any Apple user. Lucee in the sky with exploits In a detailed technical write-up, Maini… Source link
Read More »Cloud Attacks Are Bypassing MFA, Feds Warn – Threatpost
CISA has issued an alert warning that cloud services at U.S. organizations are being actively and successfully targeted. The Feds are warning that cybercriminals are bypassing multi-factor authentication (MFA) and successfully attacking cloud services at various U.S. organizations. According to an alert issued Wednesday by the Cybersecurity and Infrastructure Security Agency (CISA), there have been “several recent successful cyberattacks” focused on compromising the cloud. Most of the attacks are opportunistic, taking advantage of poor cloud cyber-hygiene and misconfigurations, according to the agency. “These types of attacks frequently occurred when victim organizations’ employees worked remotely and used a mixture of… Source link
Read More »Researcher Builds Parler Archive Amid Amazon Suspension – Threatpost
A researcher scraped and archived public Parler posts before the conservative social networking service was taken down by Amazon, Apple and Google. A security researcher said she has scraped and is archiving 99 percent of Parler’s public posts, as the social-media network goes offline following suspensions from Amazon, Apple and Google. Archived content includes public posts from the social-media site. These posts reportedly included Parler video URLs made up of raw video files with associated embedded metadata – and precise GPS coordinates of where the videos were taken, sparking privacy concerns about the service’s data collection. The researcher behind the archival… Source link
Read More »‘Jeopardy’ Picks Katie Couric as Next Guest Host After Ken Jennings
Photographed by Nathan Rocky for TheWrap “Jeopardy!” has lined up its next guest host, according to a report from the Los Angeles Times on Wednesday. Katie Couric has signed on to host the popular quiz show for a week’s worth of episodes, making her the second guest host after Ken Jennings, according to the paper. Representatives for the show and for Couric did not immediately return TheWrap’s request for comment. Also Read: Listen to Alex Trebek’s Touching Message in One of His Last Ever ‘Jeopardy!’ Episodes (Video) “Jeopardy!” is currently airing its final string of episodes with Alex Trebek at the podium, with his final turn as host to air on Friday, Jan. 8. The episodes were taped last October, before Trebek… Source link
Read More »Ortus Solutions Releases Its Second Lucee ColdFusion (CFML) AMI
The Windows 2019+Boncode+Tomcat AMI will give users a complete, modern and hardened stack for the Lucee CFML (ColdFusion) server THE WOODLANDS, Texas (PRWEB) December 30, 2020 Ortus Solutions, Corp announced today the release of the Windows 2019+Boncode+Tomcat AMI. Complete with optimized Windows 2019 and Tomcat 9 settings, CFML applications will be highly performant and secure. This stack will allow users to build high performant production or development machines based on Lucee 5.3.6.61 CFML and with CommandBox 5 as the CLI companion. “We are so excited to release our Windows 2019 Lucee AMI to the Amazon Marketplace. This is another step completed in our initiative to build and offer several cloud server images to help our customers run highly scalable… Source link
Read More »Out of the Bubble: Now or Never? – Mad In America – James Moore
The difference between public image and first-hand inside knowledge applies to all areas of life. Nobody can have a personal experience with each and every social institution; for most of them, we rely on what we hear, read, and watch. For example, I have never encountered police brutality, but I read about it in the media; media coverage, in turn, helps me contextualize stories that I hear from my non-white friends. Just by glancing at headlines, I immediately become aware that there is a wide range of positions on the current state of the American police. In all major media outlets, I can see op-eds, letters, and comments written by activists of all stripes; by victims of police brutality; by victims of crime who praise police or decry its inefficiency; by police employees who defend… Source link
Read More »Safe alternatives to nuclear fission
Philo Farnsworth wasn’t working on “cold fusion.” He was working on nuclear fusion (hot plasma). Work on his “Fusor” reactor design continues with the Polywell reactor, but remains 20-plus years in the future. It is irresponsible for Don to bring up nuclear fission without mentioning the seriousness of its radioactive byproducts, some of which have a half-life of 200,000 years. Radioactive reactor garbage is an environmental catastrophe that has no solution. Chernobyl accidents will always happen. Don’s prejudices against batteries are not based on scientific fact. The 100MW South Australian Hornsdale Power Reserve is just one of many successful utility battery storage installations. Cheap battery recycling is a strategic part of Tesla’s corporate plan. Our leaders let the… Source link
Read More »EU announces funding for four next-gen clean energy technologies
Image: EIC The European Commission’s European Innovation Council has awarded funding for research on four ‘radically new’ future clean energy technologies. The funding under the new Pathfinder scheme for deep-tech research and innovation is aimed to support visionary ideas that may – or perhaps may not – translate into reality. The four clean energy projects, which will run over the next three to four years, are focussed on clean energy production, power harvesting for sensors, energy recovery from waste heat and chemical energy storage. HERMES – hydrogen-metal systems for clean energy The HERMES project is revisiting the cold fusion concept, which emerged back in 1989 with the claimed discovery by the electrochemists… Source link
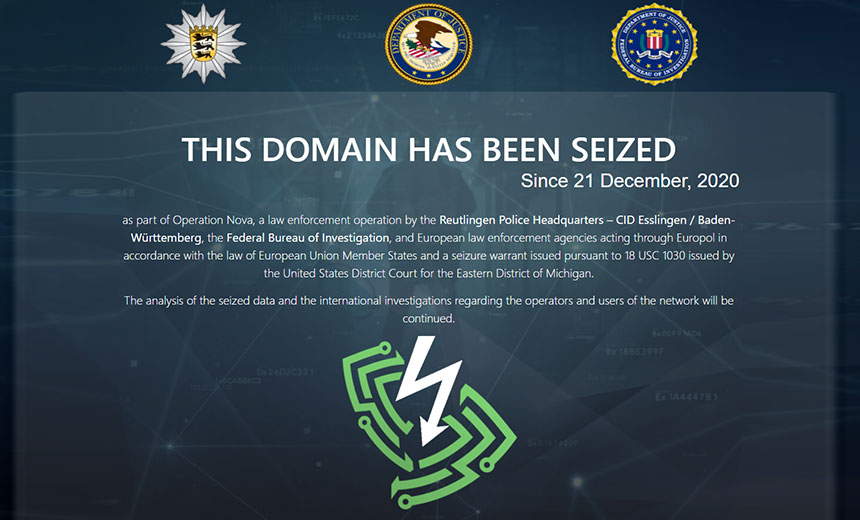
Read More »Police Dismantle Cybercrime ‘Bulletproof Hosting Service’
Cybercrime , Fraud Management & Cybercrime , Fraud Risk Management Authorities Shut Down VPN That Supported Illegal Operations Doug Olenick (DougOlenick) • December 22, 2020 … Source link
Read More »